ZYTE Disaster Recovery
Service-interrupting events can happen at any time. From human error to natural disaster there is always the possibility that the ZYTE application could go down and/or important data could be corrupted, hacked, or lost. This document outlines what ZYTE has planned to both protect and recover from a disaster and what you, our client, can also do to protect your digital assets.
Data
There are different categories of data which pose different risks and can be protected in different ways:
The ZYTE application software
Client’s digital assets created from ZYTE calls
Client’s personal information which includes organisation name, personal name, phone number and email address.
Client’s credit card information
Client feedback and interaction via social media channels and help desk
Security
Passwords: to protect Client’s accounts including Digital Assets, ZYTE uses One Time Passwords (OTP) which is two factor authentication and means there is no passwords or other information such as your first date or your Mother’s maiden name saved anywhere. The only way a Hacker can get into a client’s account is by being in physical possession of their mobile phone.
If your mobile phone is lost or stolen you are welcome to contact ZYTE and we will temporarily block your account.
Encryption & Multi Zone Backup
Zyte uses encrypted AWS RDS Postgres with a secondary and multi Availability Zone capability to store the ZYTE application software, Client’s personal information, and Client’s digital assets. Therefore, all client data including digital assets is encrypted so that if a Hacker were able to break into the ZYTE cloud on AWS no client data would be visible without breaking encryption.
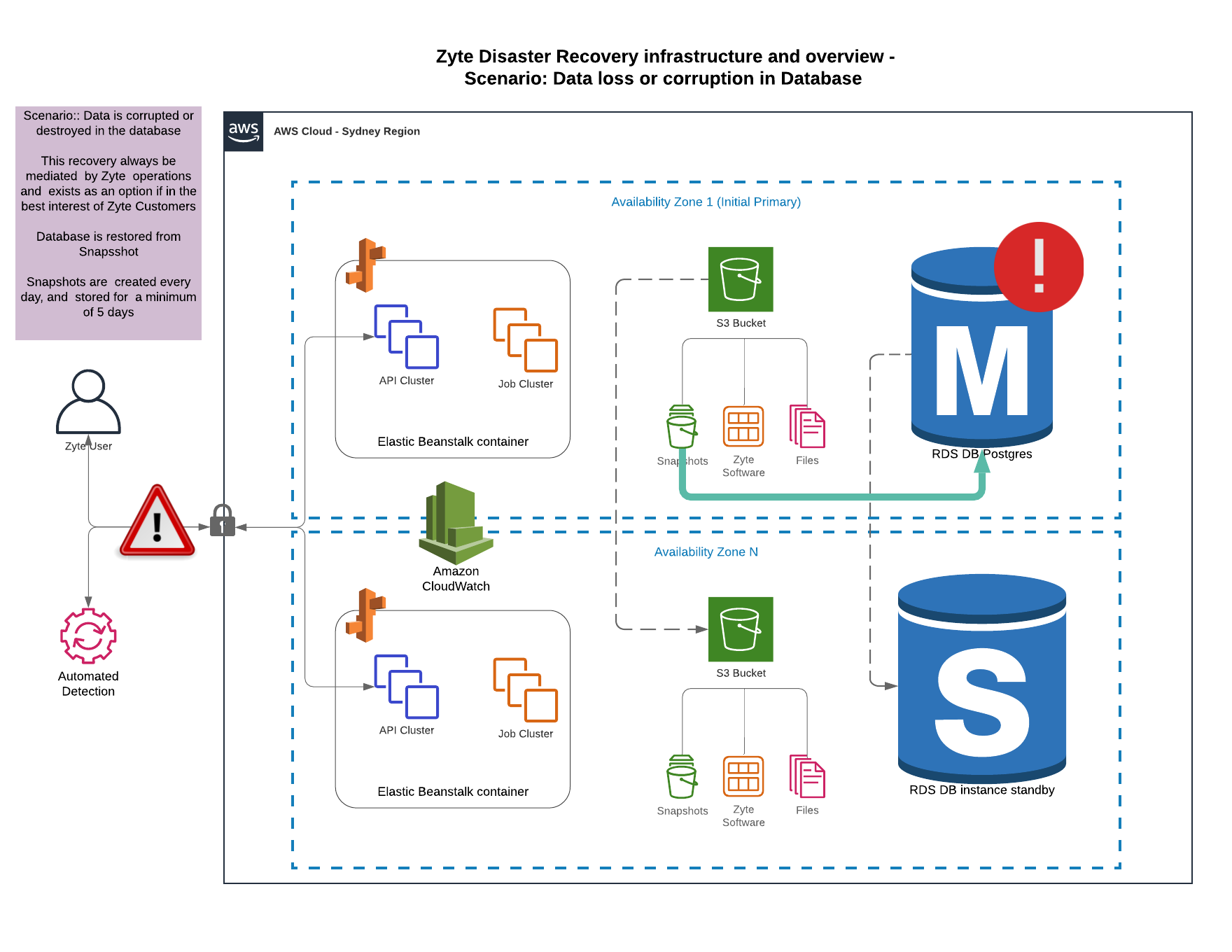
In the event of an outage in the primary servers we fail over to the secondary In the event of a more serious data loss (e.g. data in live is corrupted or our Australia AWS data centers are both destroyed during war or natural disaster - historical backups allow rollback at least 48 hours . In this event, all data will be restored to the selected point.
Long restores where client fault means that data has been corrupted over a long period may be available but are not guaranteed.
Encryption also means that no ZYTE employees or subcontractors are able to access Client’s digital assets.
Backups: ZYTE runs automated backups every 24 hours, and retains them a minimum of 5 days
Choice of data storage
Enterprise Clients that are concerned with the security of their digital assets have several options:
Remove your digital assets from the ZYTE AWS cloud and protect them on your own system.
Provide your own backup of your digital assets by downloading them at the end of each call and putting a copy on your own system.
Purchase automated API integration to transfer your digital assets from the ZYTE cloud server to your own server.
Purchase ZYTE’s backup cloud server space in an alternative jurisdiction so that you have your digital assets stored on ZYTE’s AWS Cloud in Sydney, and backed up to a second AWS server in another location.
Protecting Credit Card information
To manage and process non Enterprise subscriptions we use the services of Chargebee and Stripe who may hold your credit or debit card information for the purposes of renewing your ZYTE subscription. We do not have access to any of your card details that you enter into Chargebee or the Stripe processing systems. Both Chargebee and Stripe are PCI Level 1 certified service providers.
ZYTE application software protection
Zyte’s platform is deployed over clusters of redundant servers, the images of which are stored in encrypted storage (S3). This means that the platform can quickly scale capacity in line with demand, or adapt to problems in an Availability Zone. In addition, Zyte’s full source code is stored in encrypted repositories off-site
Cyberattack: Zyte uses industry standard infrastructure to protect against cyber attacks including DDOS, Password hacking, MITM attacks and more. Zyte also holds insurance against cyber attacks.
Accidental Deletion of Data
The ZYTE system uses soft deletions followed by hard deletes to help mitigate user error, in several areas. The ZYTE database has both a live secondary and regular database backups (every 24 hours, retained for at least 5 days).
Infrastructure
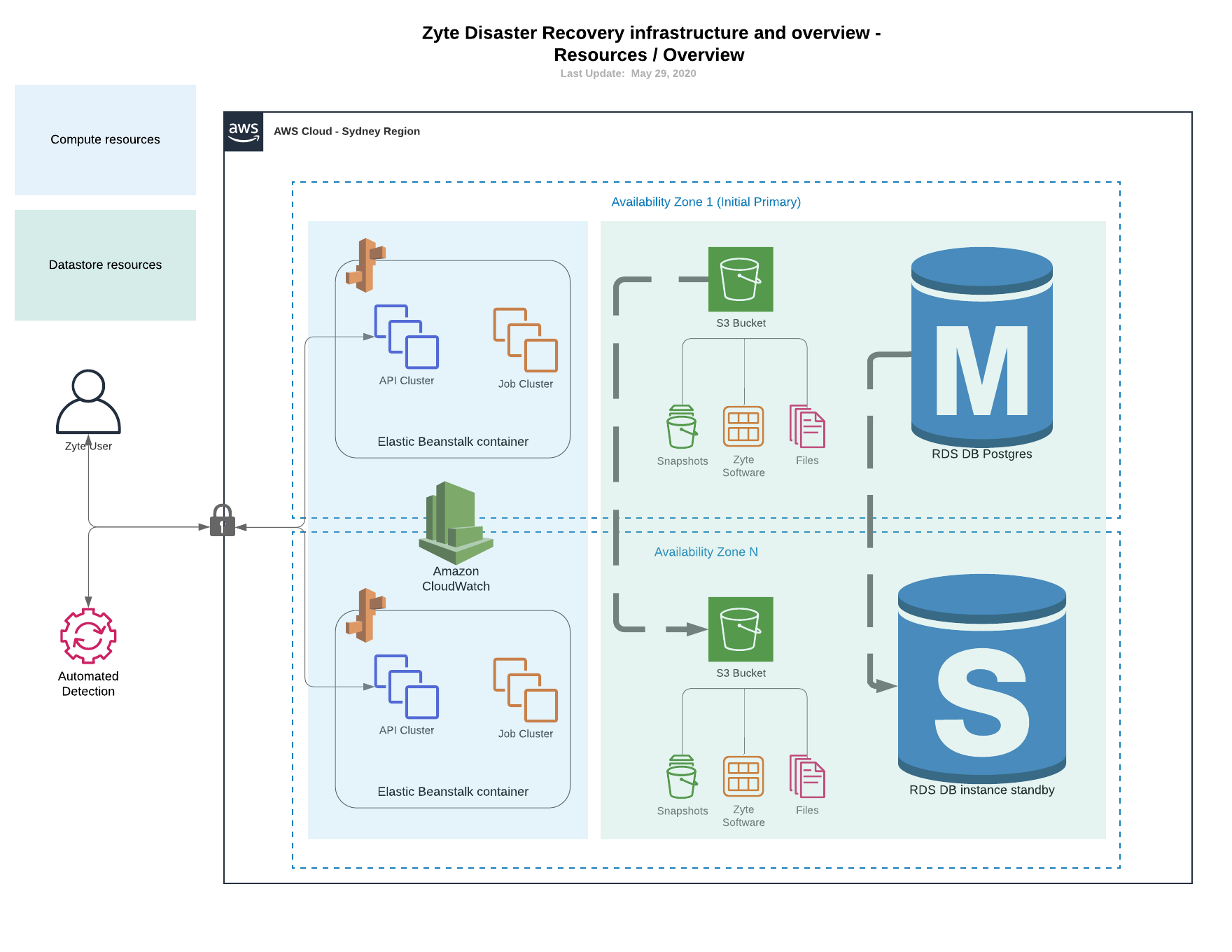
As explained in the diagrams below, ZYTE uses AWS in Sydney to host and backup the ZYTE software and your digital assets that you choose to remain hosted on the ZYTE cloud.
Showing the ZYTE AWS storage infrastructure in normal operating mode:
Showing the ZYTE AWS compute infrastructure in normal operating mode:
Showing what happens when the ZYTE AWS infrastructure detects an outage
Showing what happens when the ZYTE AWS infrastructure has a partial or full failure
Showing what happens when the ZYTE AWS infrastructure when there is data loss or corruption.
Geographical spread of Data Centres
Geographical location of AWS data centres in Sydney